Download Prey 1.11.5 Download | TechSpot

Download Free Prey 1.11.5 Download | TechSpot
It is lightweight, open source software and free for anyone to use. And it just works.
How it works
Basically, you install a little agent in your PC or phone, which quietly waits for an external signal to wake up and work its magic.
This signal is sent either from the Internet or via an SMS message, and allows you to gather information about the device’s location, hardware and network status, and optionally trigger specific actions on it.
100% geolocation aware
Prey uses either the device’s GPS or the nearest WiFi hotspots to triangulate and fix the location. It’s shockingly accurate.
Know your enemy
Take a photo of the thief with your laptop’s webcam so you know what he looks like and where he’s hiding. Strong evidence.
No unauthorized access
Completely lock the PC, rendering it unusable unless a specific password is entered. The guy won’t be able to do anything!
Wifi auto connection
If enabled, Prey will attempt to connect to the nearest open WiFi hotspot when no Internet connection is found.
Watch their movements
Take a screenshot of the active session * if you’re lucky you might catch the guy logged into his email or Facebook account!
Scan your hardware
Get a complete list of your PC’s CPU, motherboard, RAM and BIOS information. Works great when used with active mode.
Light as a feather
Prey has very few dependencies and doesn’t even leave a memory footprint until it’s activated. We care as much as you do.
Keep your data safe
Hide your Outlook or Thunderbird data and remove any saved passwords so no one can see your stuff.
Full automatic update
Prey can check its current version and automatically download and update itself, so you don’t have to manually reinstall every time.
What is new
- Android version updated to 2.4.8
Bitlocker disk encryption
Use our new Disk Encryption tool to easily encrypt data on compatible Windows devices remotely using Windows’ native BitLocker tool.
Businesses with fleets using Windows as their operating system can now take advantage of Microsoft’s original BitLocker disk encryption tool using Prey! Let us introduce you to our new disk encryption action. This tool allows you to easily enable BitLocker’s disk encryption remotely on compatible devices (Windows 10 Pro, Enterprise or Education) and protect the data on their hard drives!
BitLocker is a built-in encryption tool that comes with Windows 10 Pro, Enterprise or Education and does not need to be installed or purchased separately.
This new tool has been added to our Enterprise plan and is the next step to better help organizations secure their data. Encryption is an important risk-reducing agent! Data theft, data breach or device loss will not result in compromised data if said information is encrypted.
How to use the Disk Encryption Tool
This action will be available on all Windows 10 devices running a Windows Pro, Enterprise, or Education edition and with hardware that has TPM (Trusted Platform Module). To turn on BitLocker:
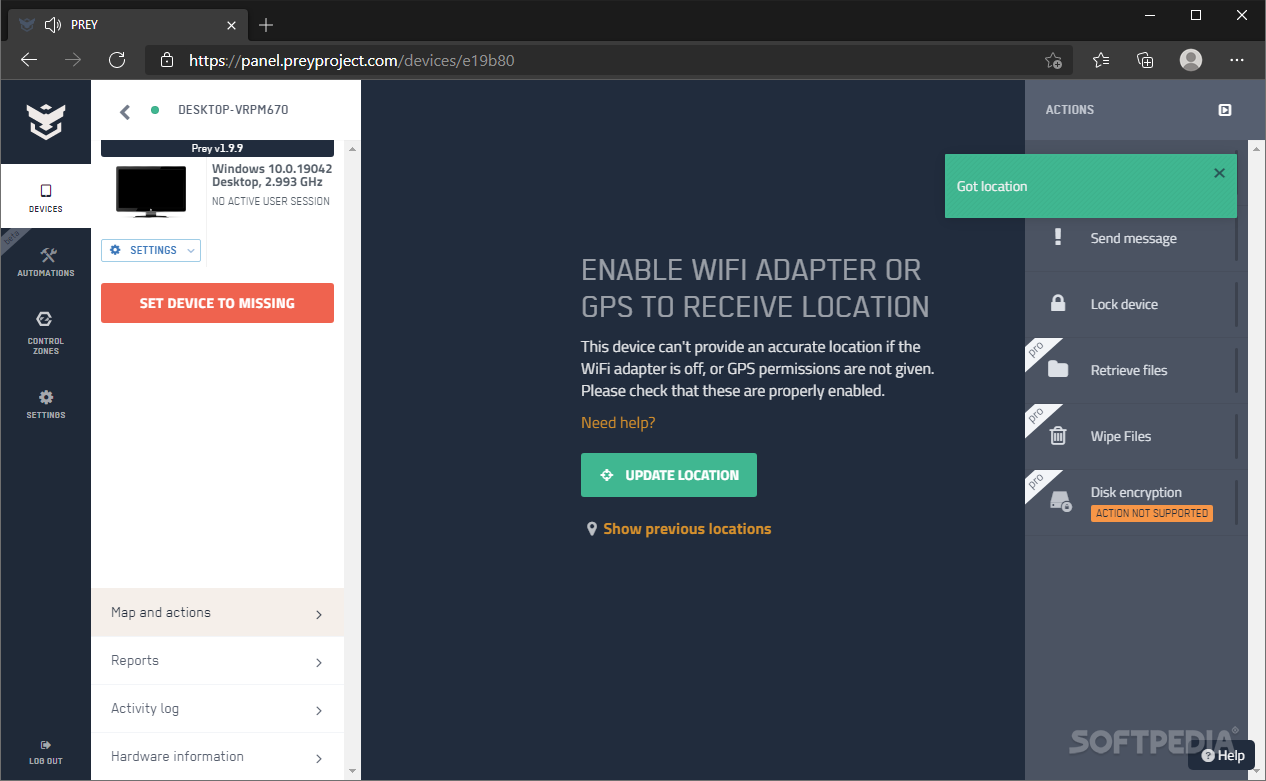
1) Find a compatible Windows device in the Prey control panel and access the individual view by clicking on the device list. Once there, you can find the Disk Encryption action on the action bar on the right.
2) Click the action’s button to start the process. You must select the drives on your computer that you want to encrypt with BitLocker.
3) Select the encryption method you want to use. Selecting ‘Full Disk’ takes longer but protects the entire disk (unused and used). This is ideal for computers that are in active use; on the other hand, choosing “Used space only” will be faster, but it does not protect unused space. This is ideal for brand new computers that have no data saved yet.
4) Finally, select the encryption standard. AES_128 is ideal for fixed internal drives and XTS_AES128 is ideal for removable drives such as a flash drive. This option represents the type of encryption used.
5) Click Start encryption to apply!
What will happen next?
Prey will reach out to the device and, once connected, will ask BitLocker to start the encryption process. You can click the action to see a progress bar and follow the encryption process as it protects the selected drive.
Note that the encryption process is not instantaneous, as Windows must encrypt all available data as a whole. Completion time will vary according to computer specifications and disk data size.
The encryption process is ongoing and the device can be used continuously even with encryption, and when it is complete, all newly generated data will be encrypted by default. However, this means that your computer’s performance will be slightly modified as a smaller portion of the processing power will run this continuous encryption process. The recovery key (or encryption key) and disk password will be available on your device’s hardware details in your account.
How to decrypt a boot encrypted disk
- The decryption process is quite simple. You can find the Decrypt option in the same action as before, Disk Encryption.
- Find a Windows device in your Prey account that was previously encrypted with the same platform and click on it to access its individual view.
- Open the Disk Encryption utility and select the target disks to decrypt.
- Click Decrypt and Prey will start the process.
What will happen next?
Prey will connect to the Windows device and disable BitLocker, and start the decryption of the selected disks. This process takes anywhere from 20 minutes to a couple of hours depending on the size of the disk and the characteristics of your computer. If the device is turned off, it will be interrupted and resumed when it is turned on again.