Apple allows part of Big Sur’s network traffic to bypass firewalls

Patrick wardle
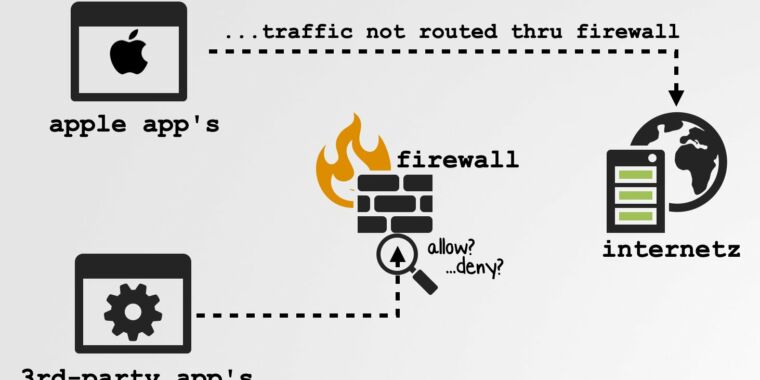
Firewalls aren’t just for corporate networks. Many people who are concerned about security or privacy also use them to filter or redirect traffic that comes in and out of their computers. Apple recently made a major change to macOS that thwarts these efforts.
Starting with macOS Catalina released last year, Apple added a list of 50 Apple-specific apps and processes that were supposed to be firewall-exempt like Little Snitch and Lulu. The undocumented exemption, which only came into effect when firewalls were rewritten to implement changes in Big Sur, was first revealed. in October
In Big Sur, Apple decided to exempt many of its applications from routing through frameworks that now require the use of third-party firewalls (LuLu, Little Snitch, etc.) 🧐
Q: Could it be (ab) used by malware to bypass these firewalls as well? 🤔
R: Apparently yes, and trivially 😬😱😭 pic.twitter.com/CCNcnGPFIB
– patrick wardle (@patrickwardle) November 14, 2020
“100% blind”
To demonstrate the risks associated with the move, Wardle, a former NSA hacker, showed how malware developers could take advantage of the change to end a proven security measure. He configured Lulu and Little Snitch to block all outgoing traffic on a Mac running Big Sur, then executed a small programming script that contained exploit code that interacted with one of the apps exempted by Apple. The Python script had no problem reaching a command and control server that you configured to simulate a server commonly used by malware to filter sensitive data.
“He kindly asked (coerce?) One of Apple’s trusts to drive network traffic to a server controlled by an attacker and he could (ab) use it to exfiltrate files,” he told me. Wardle, referring to the script. “Basically, ‘Hey, Mr. Apple Item, could you please send this file to Patrick’s remote server?’ And I would agree. And since the traffic was coming from the trusted element, it would never be routed through the firewall… which means the firewall is 100% blind.
Wardle tweeted part of a bug report you sent to Apple during the Big Sur beta phase. He specifically warns that “essential security tools, such as firewalls, are ineffective” with the change.
Apple has yet to explain the reason for the change. Incorrect firewall settings are often the cause of software that does not work properly. One possibility is that Apple has implemented the measure to reduce the number of support requests received and improve the Mac experience for people who are not ready to set up effective firewall rules. It is not unusual for firewalls to exempt their own traffic. Apple may be applying the same reasoning.
But the inability to override settings violates a rule of thumb that users should be able to selectively restrict traffic from their own computers. In the event that a Mac is infected, the change also gives hackers a way to avoid what is for many an effective mitigation against such attacks.
“The problem I see is that it opens the door to do exactly what Patrick has demonstrated … malware writers can use this to infiltrate data into a firewall,” said Thomas Reed, director of Mac and mobile offerings for security firm Malwarebytes. “Plus, it’s always possible that someone has a legitimate need to block some of Apple’s traffic for some reason, but that removes that ability without using some sort of hardware network filter outside of the Mac.”
People who want to know which apps and processes are exempt can open the macOS terminal and enter sudo defaults read /System/Library/Frameworks/NetworkExtension.framework/Resources/Info.plist ContentFilterExclusionList.
NKE
The change came when Apple ditched the macOS kernel extensions, which software developers used to make applications interact directly with the operating system. The disapproval included NKE, short for Network Kernel Extensions, which third-party firewall products used to monitor inbound and outbound traffic.
Instead of NKE, Apple introduced a new user mode framework called the Network extension framework. To work in Big Sur, all third-party firewalls using NKE had to be rewritten to use the new framework.
Apple representatives did not respond to email questions regarding this change. This message will be updated if they respond later. In the meantime, those who wish to cancel this new exemption will have to look for alternatives. As Reed pointed out earlier, one option is to trust a network filter that runs from outside your Mac. Another option is to trust PF, or Packet filtering firewall built into macOS.



